Data breaches are becoming a huge problem, and it’s scary to think about how easily they can bring down an entire organization’s security. If you’re feeling unsure about how to protect your company’s sensitive data, don’t worry—you’re in the right place.
In this blog, we’ll dive into what data breaches really are, how they happen, and most importantly, what you can do to prevent them.
Let’s have a look!
What is a Data Breach?
A data breach happens when someone steals or gets access to private information without permission. This is often done on purpose through cyber-attacks like hacking, phishing, or using harmful software. The stolen information can include personal details, bank account data, or business secrets, which might be misused, sold, or shared publicly.
Data breaches are a big problem because they put your privacy and security at risk. They can lead to identity theft, money loss, or damage to a company’s reputation. These incidents show why it’s so important to use strong security measures to keep personal and sensitive data safe.
How Data Breaches Happen
It’s not always as simple as a hacker breaking into a system—they can occur in a variety of ways, and sometimes the cause is something we least expect.
Let’s take a closer look!
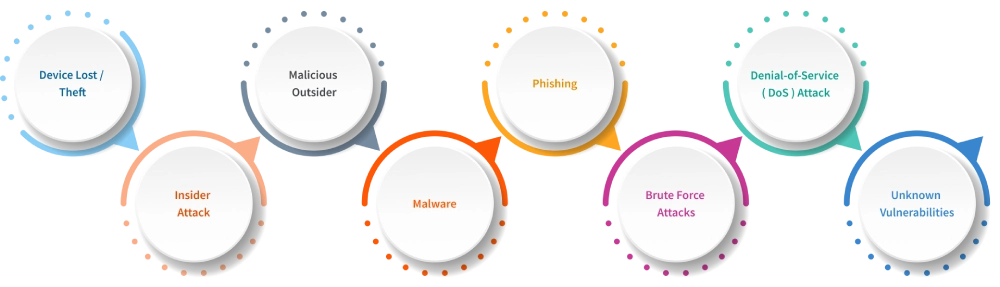
1. Device Lost / Theft
Data breaches can happen if a device is lost or stolen. If devices such as phones, laptops, or tablets are lost, anyone who might find them can access the confidential information that is present in the devices. It happens when the device isn’t properly secured.
For instance, a device that has no password, or doesn’t have good security measures, is most likely to fall for this data breach. Even if devices maintain good security measures, data breaches can still happen. Many experienced hackers find different ways to bypass security and steal personal data.
2. Insider Attack
Insider attacks are the most dangerous attacks that ever happen in an organization. An insider attack happens when an employee, contractor or anyone with authorized access to the organization’s data intentionally exposes the information. This is also known as malicious insider, where an individual who shares their company’s private data with third parties.
For example, they could take financial documents or a list of clients and sell them to another business. Or they could provide hackers with important details, such as passwords or information in exchange for money. These attacks are normally triggered when employees feel unfairly treated, frustrated or when they seek to grow financially.
3. Malicious Outsider
Malicious outsiders are individuals or groups not associated with a company who attempt to gain unauthorized access to its systems. They try various ways to access systems. We’ll discuss some of the major methods they use!
4. Malware
Malware is harmful software which is used to damage, or steal information from a network or device. A device’s operating system, hardware, software, or any network may contain some weak areas that hackers can take advantage of weaknesses to add malware. This malware includes spyware, viruses, ransomware, etc., which are used to damage the system and steal information. Especially, spyware can secretly access personal data without you noticing. This malware can spread through infected email links, and websites. Once inside, it can even track keystrokes, lock your files and give access to hackers secretly, often without you realizing until it’s too late.
5. Phishing
Phishing is a type of online attack where hackers try to trick employees to gain sensitive information such as passwords, credit card details, etc. from them. They usually pretend to be trusted people or companies and send messages, fake emails, or create fake websites. These fake links or attachments may lead to harmful sites that steal your information or put malware on your device. Phishing is one of the most common ways hackers get access to systems.
6. Brute Force Attacks
Brute force attacks happen when hackers use software tools to guess your password or encryption key by trying all possible combinations until they find the right one. These attacks are usually slow, but now they have become faster because computers are more powerful now. Since computer processing speed is growing, these attempts can be tried in a shorter amount of time. If your password is weak and easy to guess, it could take seconds for them to crack it and boom! – They’ve gained full control of the system.
7. Denial-of-service (DoS) Attack
A DoS attack happens when a server, system, or network gets overwhelmed with huge traffic, which becomes hard to respond/handle real requests. This makes the whole system crash. Hackers use these attacks to disrupt services, create downtime, and even draw attention away from other harmful actions (secretly stealing data, installing malware, etc.) A DDoS (Distributed Denial-of-Service) attack makes things worse by using many hacked systems to launch the attack at the same time, making it even harder to stop.
8. Unknown Vulnerabilities
Unknown vulnerabilities, also called zero-day vulnerabilities, are weaknesses in software that developers or users are unaware of. Hackers took advantage of these security gaps before they were fixed, often with several consequences. Keep your systems updated and use strong tools to protect yourself.
Protect Your Data from Breaches!
Stay secure and safe guard with Time Champ data loss prevention!
Sign Up for FreeBook DemoWhat Kind of Data Do Attackers Target In Data Breaches?
Every hacker aims to access private data, whether it belongs to an organization or an individual. In data privacy breaches, attackers usually focus on personal data such as names, email addresses, social security numbers, phone numbers, etc. Hackers use this data to impersonate someone, access bank accounts, defraud or sell the details on the internet. They also trick people into giving up more personal info through scams.
financial information like bank account numbers, credit card details, and payment login info is a huge target for thieves too. Attackers use this data to make unauthorized purchases, set up fraudulent transactions, or steal funds directly from the victim’s accounts. They often sell stolen financial details on the dark web, where others use it to make fake credit cards or hide stolen money.
Additionally, they target internal login credentials such as usernames, passwords, etc. These credentials give direct access to the hackers to enter into the company’s systems and data, which potentially leads to further breaches, and the leakage of business data.
Attackers also steal health info, like your medical records, insurance numbers, and prescriptions. If you’re wondering what they might do with these records, they could sell them online or use them to commit fraud. Most importantly, attackers aim to steal a business’s confidential information such as future plans, business secrets, etc. They could spill this data online or sell it to competitors just to make a quick buck.
These hackers can cause some serious consequences, which drastically damage reputation and financial growth.
Real-life Examples of Data Breaches
Data breaches are serious business—they don’t just affect companies, they can shake entire industries.
Let’s take a look at a few incidents that have really made history in the world of data breaches!
1. Kaseya, 2021
On July 2, 2021, a major ransomware attack hit Kaseya, a company that provides IT management software, affecting over 1,000 businesses worldwide. The hackers, part of the REvil group, exploited a vulnerability in Kaseya’s VSA software, which is used by managed service providers (MSPs) to manage IT systems for many clients. The attack locked companies out of their own files and systems, demanding $70 million to unlock them. While the hackers didn’t steal personal data, the breach caused significant downtime for small and medium-sized businesses. Kaseya immediately fixed the problem and worked with experts to reduce the damage. They also advised affected customers to disconnect their systems to prevent further spread.
2. Yahoo
Yahoo suffered two massive data breaches, among the largest in history. In 2013, hackers took information from all 3 billion accounts, like names, email addresses, phone numbers, birthdays, and passwords. In 2014, another breach hit 500 million accounts and leaked similar details. Yahoo didn’t tell people about these breaches until 2016. After that, they made users change passwords and stopped using old security questions to improve safety.
3. Equifax
In 2017, Equifax, a big company that tracks credit, had a huge data privacy breach. Hackers stole personal information from 147 million Americans, 15.2 million people in the UK, and around 19,000 Canadians. Cybercriminals identified a vulnerability in Equifax’s web server between May and July, and they stole personal data including their names, social security numbers, dates of birth, addresses, etc. Equifax didn’t tell anyone about the breach until September, months after they found out. Later, Equifax settled for $700 million to cover the government and those affected.
4. Marriott
The Marriott data breach happened in 2018 and affected about 500 million guests. Hackers targeted Marriott’s Starwood reservation system, which it had bought in 2016, and had been inside the system since 2014 without anyone noticing. The breach exposed fundamental data such as names, addresses, phone numbers, emails, passport numbers, dates of birth and credit card information. Marriott found out the breach in 2018 and quickly informed the public saying that hackers had stolen data from about 500 million guests, and offered free credit monitoring to the affected guests. The fact that the breach went unnoticed for almost four years raised big concerns about how safe personal data is.
5. Facebook
Facebook had another leak of data for over 500 million of its users, which included their name, phone number, email, date of birth, and sometimes even their location. Attackers found an issue in Facebook’s “contact importer” tool and used it to collect the data. Hackers also stole personal data of 533 million users, and the Ireland Data Protection Commission opened an investigation to identify if Facebook violated the state’s privacy laws. Although the breach didn’t expose any passwords or financial information, it has raised some deep concerns about data safety. Meta (formerly Facebook) was fined in November 2022 and has been trying to strengthen security since then.
6. LinkedIn
In 2021, it was found that data from 700 million LinkedIn users, almost 93% of its members, was being sold online. These details included names, phone numbers, and email addresses, job details, as well as links to other profiles on social networks. LinkedIn said no private information like passwords or financial details were exposed. The data was collected by automated bots that scraped publicly available profiles, not through a hack. LinkedIn explained that this wasn’t a new breach, but a large amount of public data being gathered, and they are working to stop it from happening again.
Avoid Costly Data Breaches That Impact Millions!
Use Time Champ to protect data and manage teams securely.
Sign Up for FreeBook DemoHow to Prevent a Data Breach?
After seeing the damage data breaches can cause, you wouldn’t want your organization to be the next headline, would you?
No, right?
It’s time to step up and implement the right prevention measures to protect your data.
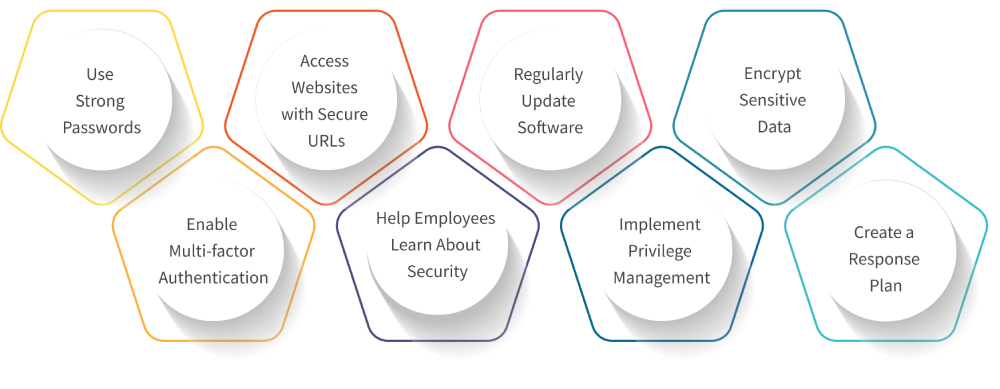
1. Use Strong Passwords
The main step is to stop using weak passwords. This is the most common cause of data breaches. Many employees often use the same passwords for every other social platform, which becomes much easier for attackers to steal information. They can easily apply brute-force attack to gain access to multiple accounts. So, consider creating strong passwords. A strong password? It should be unique, long (at least 12 characters), and mix things up with upper and lowercase letters, numbers, and special characters. Honestly, using a password manager to keep track of all those complicated passwords is a game changer. And don’t forget to update them regularly! Make sure to keep passwords tricky rather than using birthdays, etc. Keep it tricky!
2. Enable Multi-factor Authentication
Never depend solely on passwords. It is better to add an extra step to secure your accounts. Multi-factor authentication adds extra security to your accounts. It’s not just about passwords – MFA requires more than one form of verification. Even if someone steals your password, MFA stops them from getting in without a second check. This double check can be a fingerprint, a code sent to your phone, etc. This additional step makes it hard for attackers to get into your accounts and keeps your data safe.
3. Access Websites with Secure URLs
When visiting websites, make sure the URL starts with “https://” instead of just “http://”. The “s” in “https” means the site is secure and uses encryption to protect your information. This helps keep sensitive information such as passwords, credit card details, and bank details safe from attackers.
4. Help Employees Learn About Security
Even if you take good security measures, if your employees don’t know anything about cyber-security measures, it’s a waste of time. It is important to teach your employees on a security basis such as spotting fake emails, avoiding risky networks, and creating strong passwords. Try to make the training sessions engaging and fun as well to keep everyone focused and involved. When employees know how to spot threats, they become an important part of protecting the company and lower the risk of a security breach.
5. Regularly Update Software
Hackers look for weak spots in software to break into systems and steal important information. These weak spots, called vulnerabilities, make it easy for them to cause problems. To stay safe, always update your devices, apps, and security software. Updates fix these weak spots with changes called patches, which make your system stronger.
Turning on automatic updates is an easy way to make sure you don’t forget important updates. If you skip or delay updates, your system could stay open to attacks, making it easy for hackers to get in. Updating regularly is one of the easiest and best ways to keep your devices and data safe.
6. Implement Privilege Management
The principle of least privilege means giving people access only to the information and tools they need to do their job—nothing more. This helps prevent misuse, whether it’s accidental or intentional, and limits the damage if an account gets hacked. For example, an employee working in one department doesn’t need access to sensitive data from another department.
To keep this system working, regularly check what access each employee has and remove anything they don’t need anymore. Keeping access limited helps reduce the risk of a data breach and ensures that, even if something goes wrong, the damage is much smaller and easier to control.
7. Encrypt Sensitive Data
Encryption is a simple but important way to protect sensitive information, whether it’s saved on a device or being sent online. It works by turning the data into a secret code. Even if someone tries to steal it, they won’t be able to read it without the right key to unlock it.
Always use encryption on all your devices, like your computer and phone, as well as on any systems that store or send important information. Also, make sure any backup systems are encrypted, so even saved data can’t be accessed by unauthorized people. This extra layer of protection keeps your information safe from being stolen or misused.
8. Create a Response Plan
Even with security measures in place, a data breach can still occur. That’s why every business should create a response plan. The plan should include several steps such as controlling the breach, reporting it to the right individuals, informing affected employees, etc. It should also cover actions like identifying what data was stolen, changing passwords, and monitoring systems for further attacks. Regular practice ensures everyone knows what to do if a breach happens. A good plan helps reduce damage and speeds up recovery.
Prevent Data Breaches Before They Happen!
Use Time Champ to strengthen security and protect your data.
Sign Up for FreeBook DemoHow to Mitigate a Data Breach?
You can definitely reduce the impact of a data breach, even if it happens. But don’t think that means you can skip the prevention steps—being proactive is key to keeping your data safe in the first place.
Let’s look at how to minimize the damage and still stay one step ahead.
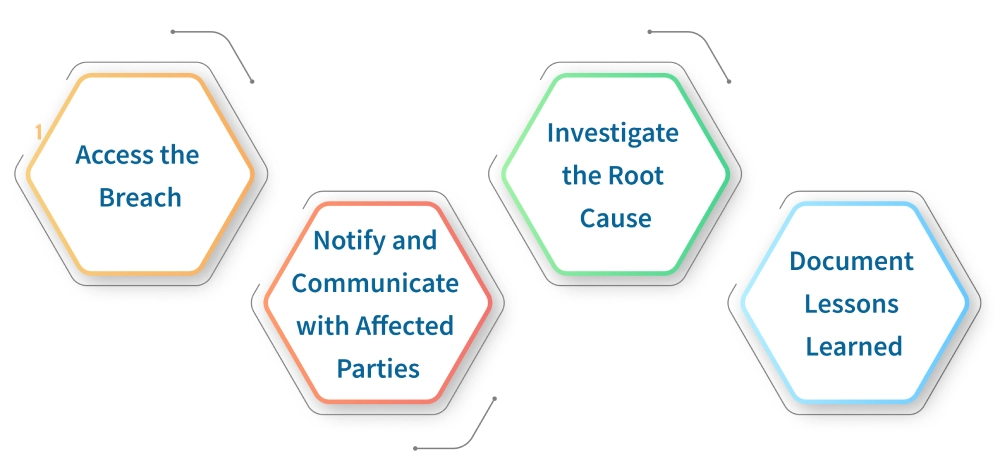
1. Assess the Breach
The first thing you need to do is figure out if a breach has really happened. If it has, the next step is to find out how bad it is. You should look at what kind of data was stolen or exposed and who it affects. This will help you understand how much harm the breach might cause. By this, you can take further actions to stop the breach from spreading, such as shutting down the affected systems or blocking access to the sensitive data.
2. Notify and Communicate with Affected Parties
After the breach is confirmed, it’s important to tell the people whose data was exposed. Inform people about what happened, what data was leaked, and how people can guard themselves. For instance, you can provide them with credit monitoring or you can advise them on how to protect their accounts. You also have to listen to the law, which may mean that you have to inform government officials or regulators within a particular time. It makes people trust you and be informed of what is happening so that they can do something about it.
3. Investigate the Root Cause
Once you have contained the breach, it’s important to understand how it happened. You should investigate what caused the breach, whether it was a software flaw, a weak password, or something else. This helps you find the weaknesses in your systems that allowed the breach to occur. By identifying the cause, you can fix those problems, so they don’t happen again. Make sure to contact experts to solve the issue and provide solutions.
4. Document lessons learned
Once the breach is over, take a moment to reflect on what happened and what you can learn. Write down everything you learned from this breach to help you avoid it in the future. Use this to make your security stronger. You might need to change your rules, improve how you protect data, or train your team to notice and handle risks better in the future. It’s also a good idea to run regular tests or simulations to make sure your organization is better prepared for the future.
Secure Your Data with Time Champ’ Data Loss Prevention!
Monitor, Manage and Secure Data with Ease.
Sign Up for FreeBook DemoFinal Thoughts
In conclusion, data breaches are harmful but you can prevent them by following some good practices such as using strong passwords, enabling MFA, and keeping your software updated. Educate your team about security issues and have a plan if anything goes wrong. If a breach happens, immediately know what happened, let those affected know, and learn from it to make it your security better. Staying proactive helps keep your data safe and risks low.
Frequently Asked Questions
Attackers focus on personal and financial data because they can use it to cheat, sell it to others, steal money, etc. For instance, they can attempt identity theft (as they can pretend to be you). If they get your credit card numbers, they can buy things without your permission.
Public Wi-Fi is often unprotected, making it easy for hackers to grab your information. It’s better to use a private connection for tasks like logging into accounts or making payments.
Phishing means hackers use different fake emails, messages or websites to fool you into giving your sensitive information, such as personal, financial, etc. Be aware of emails asking for your details, strange links, or messages saying “do this now”. Check carefully before you click or share anything.
Training employees is very important because many data problems happen when people make mistakes, like clicking on fake emails, etc. Teaching employees how to spot suspicious websites, creating strong passwords, and following safety measures can help protect the company from the hackers.

