Any data in general is already vulnerable to breaches, but what about your company’s most sensitive data? It is on the verge of being stolen every second you overlook endpoint data loss prevention.
Almost 70% of the successful data breaches out of 90% start at the endpoint devices and do you know how much a data breach costs an organization? An average of 4.88 million USD.
But how can you ensure that your data is always safe, even in an increasingly remote and interlinked world? In this blog, you will learn about what is Endpoint DLP, how it works, common challenges businesses face without endpoint DLP, and some of the best practices.
So, without any further ado, let’s just jump straight into the topic.
First and foremost, to understand any topic and its working, you need to understand what it actually means (I mean the definition), so let’s start with the definition.
What is Endpoint Data Loss Prevention?
Endpoint Data Loss Prevention (DLP) is all about keeping your company’s sensitive information safe, no matter where it goes. Whether it’s on a laptop, phone, or desktop, endpoint DLP helps ensure that your important information doesn’t end up in the wrong hands. It operates by monitoring and controlling the flow of information and data that an individual sends, receives, or transfers via any format including, cloud storage, flash drives, emails, and more.
Simply put, endpoint DLP acts like a security guard for your data and makes sure it stays protected as employees work and collaborate with each other.
Why Endpoint DLP is Essential for Businesses
Today we are not travelling the world but data is. Sensitive data is constantly being retrieved, shared, and moved around. As a result, keeping it safe has become more important. If your team is in the office, working from home, or traveling, endpoint protection is critical to safeguarding your organization’s data. Endpoint DLP safeguards your sensitive data on devices like laptops, desktops, or mobile phones, from falling into the wrong hands.
Top Benefits of Endpoint DLP Every Business Should Know
1. Shields Your Most Valuable Information
Endpoint DLP helps keep your valuable data like customer details, financial info, and company secrets safe, no matter where it’s being accessed or from which device.
2. Minimizes the Risks of Data Breaches
Data breaches can be costly and very damaging to your business. Endpoint DLP helps in preventing these risks by stopping unauthorized access to your sensitive information, whether it’s accidental or intentional.
3. Keeps You Compliant with Regulations
With laws such as GDPR & HIPAA, it’s important to protect sensitive data properly. Endpoint data loss prevention assists you in being compliant and not having to face fines and legal problems in the future.
4. Promotes Employee Responsibility
When employees are aware that their activities are being observed they will definitely follow the right data-handling procedures. Endpoint DLP encourages everyone to take responsibility for keeping data secure.
5. Secures Telecommuting
By increasing the number of virtual teams day by day, securing data on personal devices is a top priority. Endpoint DLP ensures that, when employees are working outside the office, their data stays safe.
6. Detects Insider Threats
Not all threats come from outside. Endpoint DLP can help you detect suspicious from employees, preventing potential internal risks before they turn into problems.
Common Challenges Businesses Face without Endpoint DLP
If you want to know what happens to your organization when you don’t safeguard your data, here’s what businesses deal with when Endpoint DLP is missing from their security strategy.
1. Higher Chances of Data Breaches
Without Endpoint DLP, sensitive data is more vulnerable to being accessed, stolen, or leaked. Scammers will have a free pass to your data, they don’t need to sit there for long hours to crack your passcodes, you are just making their work simpler by not protecting your data.
2. Compliance Challenges
Do you know many reputed industries have strict data protection laws such as GDPR or HIPPA? Generally, businesses struggle to follow these laws, which exposes them to penalties and damage to their reputation.
3. Limited Visibility and Control Over User Activity
When businesses can’t monitor how data is accessed and shared, it becomes nearly impossible to spot suspicious activities or stop potential leaks. This lack of visibility leaves critical information unprotected and harder to manage.
4. Data Loss from Insider Threats
Internal threats, whether deliberate or accidental, can pose a major risk. Without Endpoint DLP, companies are left with no option but to watch their employees mishandle or even steal important information that may cost the company a lot of money.
5. Inefficient Data Protection and Response
Responding to security incidents without Endpoint DLP is like trying to put out a fire without water. Without real-time monitoring and automated controls, businesses can’t act quickly to stop data leaks, resulting in slower responses and more significant impacts.
How does Endpoint DLP work?
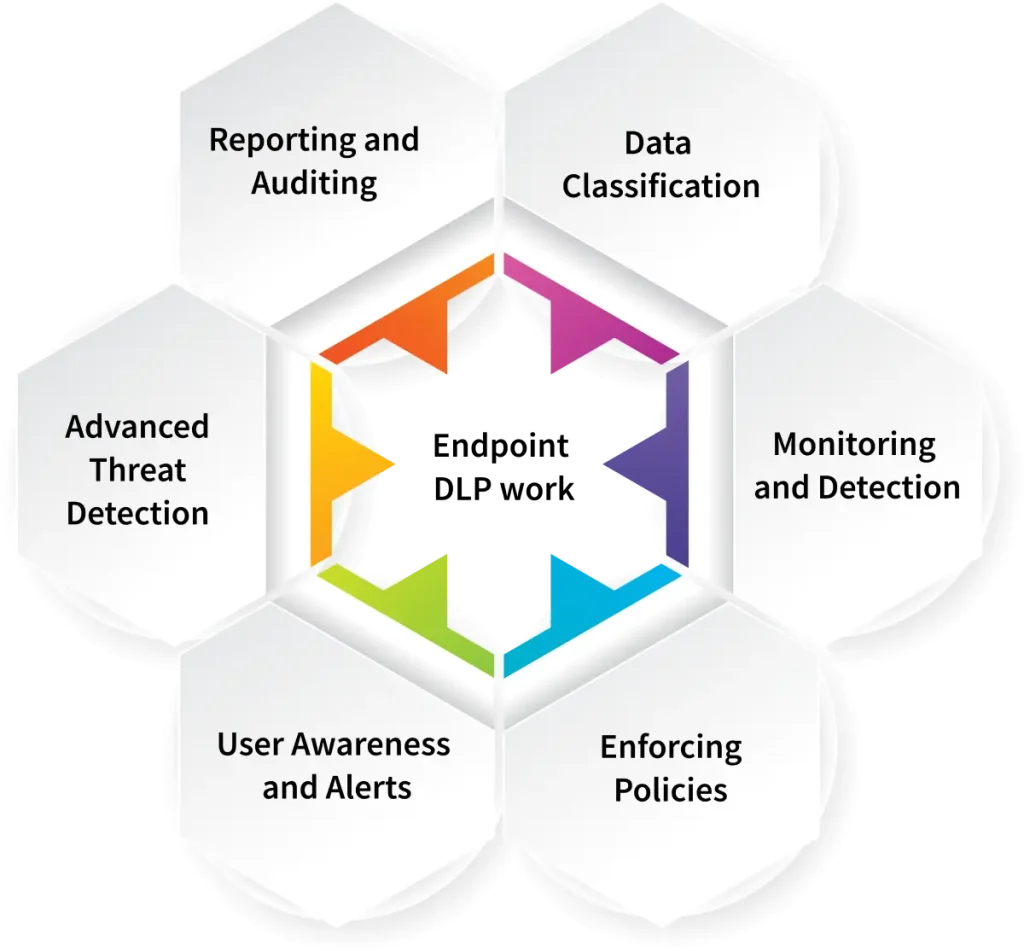
Now that you understand the importance of endpoint data loss prevention, it’s time to understand how it works as well.
Here’s a simple breakdown of how it works:
1. Data Classification
The first step is to understand which data needs the most protection of all. This could be anything from customer details and financial records to trade secrets or confidential files. Once that data is classified, DLP policies can be set in place to control who can access it and what they can do with the accessed data. This ensures only the right people are handling your most valuable information.
2. Monitoring and Detection
With DLP in place, every piece of data is constantly monitored. This includes data at rest (stored files), in motion (data being transferred), and in use (data being accessed or edited). If any data is moved, shared, or accessed in a way that violates company rules, DLP will flag it, making sure no sensitive info slips through the cracks.22
3. Enforcing Policies
If something suspicious is detected, DLP doesn’t just sit back, it takes action. Depending on your settings, it could block data from being shared, prevent access to certain files, or even encrypt them for secure sharing. For example, if an employee tries to email a confidential document to someone unauthorized, DLP can stop that from happening or protect the file so it’s sent securely.
4. User Awareness and Alerts
The goal of data loss prevention isn’t just to protect data but also to make sure your employees are well aware of the security protocols. If someone tries to break the rules, they’ll get an alert. These notifications not only stop potential breaches but also help employees understand why endpoint security is important. It’s about building a culture of responsibility and awareness, where everyone plays their part in keeping data safe.
5. Advanced Threat Detection
DLP isn’t just about preventing accidental leaks. It also keeps an eye out for unusual activity that could indicate internal threats. For example, if someone’s accessing sensitive data at non-working hours or from a device they don’t normally use, DLP will spot it. Catching these potential risks early is key to stopping bigger problems before they happen.
6. Reporting and Auditing
Finally, DLP doesn’t just protect your data, it gives businesses detailed logs and reports on any security incidents, making it easy to review what’s happened and address any weaknesses. This is especially important for staying compliant with regulations like GDPR and HIPAA, where businesses must demonstrate that they’re properly protecting sensitive data.
Key Features to Look for in an Endpoint DLP Solution
After gaining all this knowledge, if you are not already invested in an endpoint DLP solution, then what are you waiting for?
Find yourself a tool that fits best out of all available in the market, and here are some must-have features to look for. If a tool does not offer any of these features, then you know the answer right (it’s a no).
- Comprehensive Data Discovery and Classification: The first step is knowing exactly what data you have and what needs to be protected. Look for a solution that can easily classify sensitive information, from customer details to trade secrets.
- Real-Time Data Monitoring and Protection: Security isn’t a one-time event—it’s continuous. A good DLP solution will monitor data in real time, keeping it safe across all endpoints, no matter where it’s being accessed.
- Role-Based Access Control (RBAC): Not everyone should have access to everything. With RBAC, you can control who sees what based on their role, ensuring sensitive data stays in the right hands.
- Policy Enforcement and Customization: Every business is different, so it’s important to have customizable security policies. A flexible DLP solution will allow you to tailor these policies to fit your needs, from limiting file sharing to restricting access.
- Integration with Existing Security Ecosystem: Your DLP solution should integrate smoothly with your existing security tools. A unified system makes managing threats and incidents much easier.
- Detailed Incident Reporting and Analytics: When a security incident occurs, it’s important to know exactly what happened. Look for a solution that provides clear, actionable reports and analytics to help you understand and prevent future incidents.
- Support for Multiple Platforms and Environments: Today, data is accessed across multiple devices—laptops, smartphones, and desktops. Your DLP solution should work seamlessly across all of them.
- Automated Alerts: Speed matters when dealing with security threats. With automated alerts, you can immediately respond to risks.
- User Behavior Analytics (UBA): The biggest threats don’t always come from outside. User Behavior Analytics (UBA) helps you spot unusual activities within your organization, making it easier to catch internal risks early and stop them before they grow into bigger problems.
Time Champ provides comprehensive data loss prevention features so that you can safeguard your company’s most precious data and save yourself from the loss of millions.
You can continuously track your data, keep track of device activities in real time, and get instant alerts if anything unusual happens.
Time Champ gives you a clear view of what’s going on across your team, so you can catch potential risks before they escalate. You can also spot vulnerabilities, close gaps, and take control of your company’s sensitive information. It’s like having an extra layer of security that makes sure your data stays protected, no matter where your team works from.
Best Practices for Effective Endpoint DLP Implementation
This is not a hypothetical one, but if we protect our assets no matter how small they are, then what about your company’s most valuable assets? Well, the same applies here, you need to protect it no matter how small the data is, even if it is not so useful to you, it is a treasure to your competitors. So, safeguarding the data which can be your employee information, project data, company secrets, upcoming projects, tenders, and whatnot, everything needs a proper safe space to reside.
Steps to Deploy Endpoint Data Loss Prevention Effectively
1. Start with a Risk Assessment
Before diving in, take a good look at where your sensitive data lives and how it moves around your network. Remember understanding the risks is the first step in protecting it.
2. Train Your Team on Security
The best DLP strategies rely on employees to follow security protocols. It’s essential that your team knows how to handle data properly and how to spot potential threats. Take time to train your employees so that everyone is in the right understanding.
3. Set Clear Data Handling Policies
Have a clear and simple policy around how your data should be handled, whether it is retrieved, stored anywhere, or shared. Having clear guidelines will help everyone understand what is expected of them and reduce the chance of making mistakes.
4. Choose the Right DLP Solution
The right DLP solution isn’t a one-size-fits-all. It’s important to pick one that fits well with your existing security systems and meets your exact needs. Look for something flexible, effective, and easy to integrate into your environment.
5. Implement Role-Based Access Policies
Not everyone needs access to the same data. By setting up role-based access, you can ensure that employees only have access to the data they need, keeping your sensitive information more secure.
6. Keep Track of User Activity
Monitoring how users are using your system can be useful in identifying suspicious activity or possible security threats. This way, you remain active and can easily solve problems before they become out of hand.
7. Implement Change Management Guidelines
Your DLP approach isn’t something that should just be set up once and forgotten. As your business expands and the security threats change, so should the plan. Make sure that you have a mechanism for how you are going to review your strategy from time to time.
Common Mistakes to Avoid
Even with a well-planned DLP strategy, it’s easy to fall into a few traps. Here are some mistakes to avoid:
1. Ignoring Endpoint Diversity
Employees often use different devices like laptops, desktops, and smartphones. When setting up your data loss prevention solution, make sure to account for all the devices in use across your organization. Overlooking this can leave some parts of your network exposed.
2. Skipping Regular Updates and Patches
Update your DLP system to mitigate against new forms of threats that may emerge on the market. New exploits come out often and having updates and patches ready helps defend against them. Not updating your system leaves it exposed to possible hacker attacks.
Conclusion
In conclusion, securing your company’s sensitive data should be a top priority, especially with the growing risks of data breaches and insider threats. Endpoint Data Loss Prevention (DLP) acts as your first line of defense, keeping your information safe across all devices and environments. It’s more than just preventing breaches, it’s about ensuring compliance, promoting responsible data handling, and fostering a culture of security.
With the right DLP solution and the right approach, your organization will be protected from expensive data leaks, customer trust will be preserved, and your business processes will remain uninterrupted regardless of where your employees work. Protect your data, protect your business.
Frequently Asked Questions
Endpoint data loss prevention works across multiple platforms, including mobile devices, ensuring the security of your data, no matter the device used – a laptop, a desktop, or even a mobile phone.
Endpoint data protection constantly monitors the activity of the user and data access patterns. If an employee accesses sensitive information at unusual hours or from an unauthorized device, the system flags it as suspicious.
Yes, Endpoint DLP is designed to prevent both external and internal threats. It can detect suspicious activities by employees, such as transferring sensitive files to unauthorized devices, printing confidential documents, or accessing protected data without proper authorization.
Yes, Endpoint DLP is valuable for small businesses that daily deal with customers’ or employees’ personal information. Even small organizations face data theft and regulatory compliance risks, making DLP essential for protecting against potential breaches and ensuring regulatory adherence.
Endpoint DLP is a valuable tool in a data protection plan however it would be most effective when employed alongside such preventive measures as encryption, use of secure communication channels, firewalls, and access control standards. A layered security approach provides more robust protection against various threats.







