Is your workplace at risk of suspicious activity going unnoticed? Ignoring the signs can lead to serious security breaches and a loss of trust. Learn how to identify and respond effectively to suspicious behavior, ensuring your workplace remains secure and efficient. Discover actionable strategies to protect your team and business.
What is Suspicious Activity in the Workplace?
Suspicious activities in the workplace are actions performed by employees that may be unlawful or against the company’s policies and standards, which may point to unethical or malicious intentions.
Such activities may include but are not limited to unauthorized access to information, fraud or theft, sudden behavioural changes without plausible reason, owning assets beyond their means, and indifference to company regulations.
It is crucial to prevent and report suspicious activities to avoid compromising the workplace and employees’ ethical standards and to build their trust in the organization and its management.
Common Signs of Suspicious Activity
According to a PwC survey, over 52% of the organizations have experienced some form of fraud, or economic crimes in the last two years. This statistic clearly shows why it is essential to detect such problems at an early stage to guarantee a safe working environment.
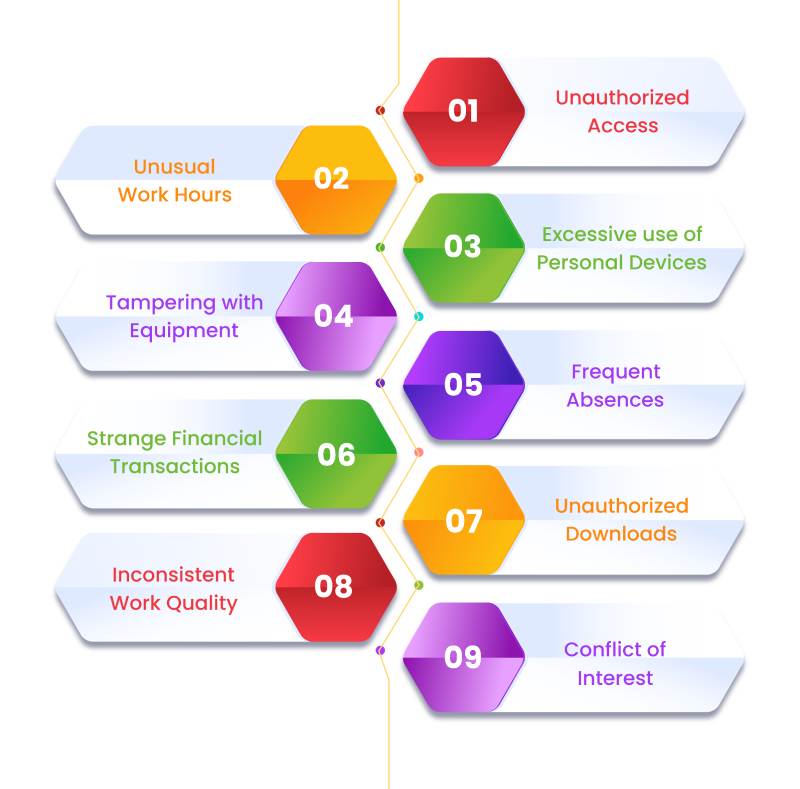
The following is a list of various forms of suspicious activity at the workplace:
1. Unauthorized Access
These are cases of people trying to access certain areas or information they are not authorized to access.
Indicators:
-
Employees attempting to unlock doors or cabinets they are not allowed to open.
-
Employees who log in with someone else’s username and password.
-
Activities that are aimed at avoiding or overcoming security measures or observation.
2. Unusual Work Hours
Employees work outside their normal hours without a clear reason.
Indicators:
-
Staff regularly stay late, come in early, or work on weekends without specific projects requiring such hours.
-
Activity in the office or on the network during unusual times.
3. Excessive use of Personal Devices
Use of personal phones or other gadgets for purposes other than work during working hours.
Indicators:
-
Employees are constantly on their phones, making private calls, or texting.
-
Use of personal laptops or tablets for tasks that should be done on company-provided devices.
-
Employees spend a lot of time on social media or browsing non-work-related websites.
4. Tampering with Equipment
Misuse of company resources or damaging company property to gain from it.
Indicators:
-
Physical signs of sabotage of computers, security cameras, or other equipment that may have been tampered with.
-
Recurrent technical glitches that seem to happen in the presence of certain people.
-
Identification of devices that are connected to the network without permission.
5. Frequent Absences
It is always a worry when an employee takes many sick days or any other form of leave from work.
Indicators:
-
Skipping work or coming in late before important dates or large projects.
-
Lack of proper documentation or plausible causes of the absence.
-
Many employees are often absent from work, come to work late, or even go home early without any valid reasons.
6. Strange Financial Transactions
Any transactions that are out of the ordinary or that cannot be explained may be fraudulent.
Indicators:
-
Any claims for reimbursement or other expenses are considered unusual.
-
Unauthorized spending or transfers of a significant amount of money from company accounts.
-
Suspected fraud, embezzlement, or any other form of financial misconduct.
7. Unauthorized Downloads or Transfers
Downloading, transferring, or copying large files or data is not justified by any business need.
Indicators:
-
Transfer large files to other devices or email addresses.
-
Downloading or using unauthorized software or file-sharing services.
-
Efforts to erase or conceal records of data transfers.
8. Inconsistent Work Quality
A sharp drop in the quality of work or the rate of work done.
Indicators:
-
Lack of punctuality, failure to meet deadlines, or making a lot of mistakes.
-
Projects not fully finished or work that must be redone repeatedly.
-
Reduced motivation or motivation to perform work-related tasks.
9.Conflict of Interest
Participating in activities that conflict with the company’s interest.
Indicators:
-
Employees who are working for other competitors or who have other businesses of their own while working for the company.
-
Interpersonal factors that affect business transactions.
-
Preferential treatment or bias in the workplace.
Impact of the Suspicious Activities on the Workplace
“Trust is like blood pressure. It’s silent and vital to good health, if abused, it can be deadly”- Frank Sonnenberg. As far as maintaining organizational trust and integrity is concerned, the part played by suspicious activity in the workplace cannot be overemphasized. From demotivating the employees to tarnishing the company’s image, the effects are not as clear-cut as one might think.
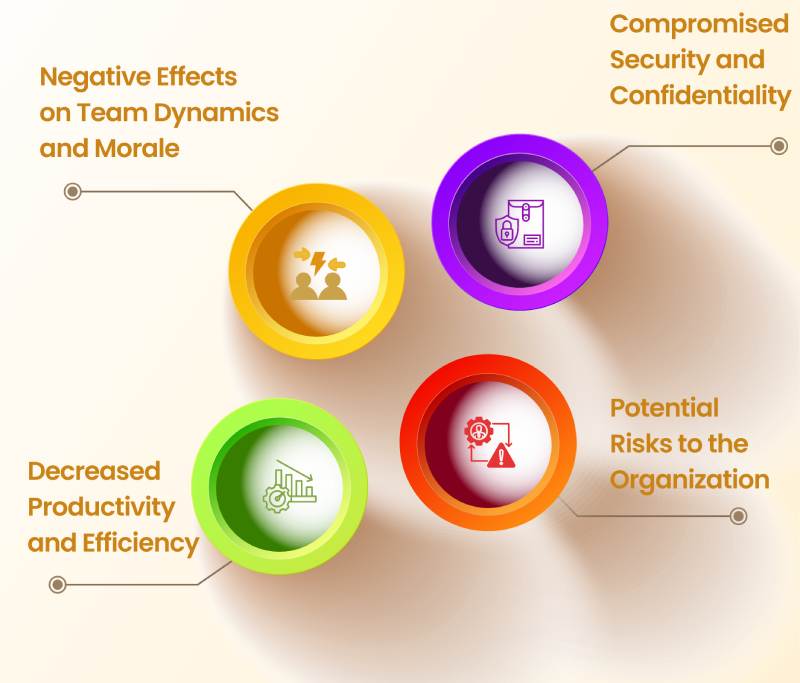
Below are the significant impacts of suspicious activity in the workplace:
1. Compromises Security and Confidentiality
Any circumstances that lead to insecurity and violation of an organization’s privacy are risky. Security breaches lead to the exposure of customer information, and this is not good for business and the law. Cybersecurity threats include malware or phishing attacks that exploit vulnerabilities in systems and networks that may result in data leakage or service unavailability. All these risks can be prevented by implementing adequate security measures, training employees, and monitoring the situation. By security and confidentiality, organizations make sure that trust is preserved, reputation is safeguarded, and operations are sustained in the increasingly digital world.
2. Potential Risks to the Organization
Insider Threats in an organization may lead to instability and slow or non-existent growth. Some of these risks are financial risks, reputational risks, legal risks, and operational risks. Financial risks are associated with poor management, changes in the market situation, or other unpredictable costs that can lead to the company’s insolvency. Loss of reputation due to scandals or negative publicity affects the customer’s trust and loyalty to the business. Legal risks include regulatory violations or legal cases that lead to fines and limitations on business operations. Operation risks such as supply chain risks or technological risks can bring business operations to a halt. It is therefore important to understand and manage these risks to protect the organization’s future.
3. Negative Effects on Team Dynamics and Morale
Negative impacts on the team and its morale can be very damaging to the organization’s achievement. Failure to communicate and conflict lead to misunderstanding and lack of collaboration which are very unhealthy for the team. The inability to trust and be supported by the team members results in a negative working environment that lowers the morale of the employees. This results in low morale which in turn results in low motivation and low productivity, deadlines are not met, and the quality of work is affected. This in turn leads to high turnover rates since the employees are likely to search for better working conditions. You should solve such problems as early as possible so that the team becomes a united and motivated one, which will be productive.
4. Decreases Productivity and Efficiency
Suspicious activities can greatly reduce the productivity and efficiency of employees in the workplace. When employees are involved in unethical practices, they shift focus from productive work and this slows down the work rate. Also, the resources and time used in handling these issues could have been channelled towards productive use. The employee must return the assets to the IT department on termination of services with the company in good working condition. In the long run, this reduces the productivity and efficiency of the organization and thus affects the performance and profitability of the business due to poor utilization of resources.
Handling and Addressing Suspicious Activity
You should be able to detect and report any form of suspicious activity in your workplace to ensure that the safety of the workplace is not at risk. To avoid negative outcomes for your organization and its image, it is necessary to know how to react to such behaviours or events.
Let’s look at how to handle and address suspicious activity:
Establish Clear Policies and Procedures
-
Create a Policy: Develop a comprehensive company policy that outlines what constitutes suspicious activity in your organization. This could include unauthorized access attempts, unusual network traffic, or behaviour that deviates from normal patterns.
-
Define Reporting Procedures: The company must clearly state how employees are supposed to report any suspicious activity. This could include specific reporting procedures like reporting through an email address or a hotline and the reports could be made anonymously if desired.
Assess and Investigate
-
Initial Assessment: In case of making a report or when there is an indication of an incidence, the first thing that needs to be done is to assess the situation to determine the severity of the incidence and its impact.
-
Investigation: Assign a group or a person to look into the matter as a possible case of fraud. This may be the IT security team, or internal or external auditors depending on the nature and gravity of the situation.
-
Gather Evidence: Collect the logs, the statements of the witnesses, and the cyber forensic data to find out how far the attack has gone and where it started.
Respond and Mitigate
-
Containment: The next step is to quarantine the spread of suspicious activity so that it does not cause more loss or access to unauthorized people. This may include quarantining the infected computers or even freezing the accounts that have been hacked.
-
Notification: If the incident is serious and of a specific nature, inform the stakeholders including the senior management, legal advisors, employees involved or affected, and the regulatory body if necessary. This could mean fixing the software, changing the security measures, or changing the rights of entry.
-
Mitigation Steps: Implement corrective actions and control actions to address the risks or problems identified during the investigation. This could mean rectifying the software, updating the security features, or altering the control access.
Review and Learn
-
Post-Incident Review: Perform a detailed analysis of the incident response process to determine the positive aspects and weaknesses. Record all the experiences and modify the policies or procedures in line with the new knowledge.
-
Training and Awareness: Promote training and awareness sessions for the employees to detect and report any suspicious activity.
Legal and Compliance Considerations:
-
Legal Counsel: Consult a legal advisor at the beginning of the process especially where the case has legal consequences or legal procedures.
-
Regulatory Requirements: Adherence to data protection laws, breach notification laws, and other laws in handling and reporting suspicious activities.
Continuous Monitoring and Improvement
-
Continuous Monitoring: We recommend monitoring the systems and networks occasionally to check for any other malicious activities in the future.
-
Incident Response Plan: Ensure the organization has a current incident response plan that includes the roles and responsibilities of the personnel, escalation procedures, and communication strategies.
Tool for Detecting Suspicious Activity
Time Champ is a time-tracking and employee-monitoring software. This tool is also used to promote accountability and ensure optimal productivity in an organization. This unique software employs sophisticated algorithms and data analysis to monitor the employees’ activity and detect any suspicious actions that might point to some misconduct or security risks.
-
Activity Monitoring: Time Champ constantly observes the activities of the employees including the usage of computers, browsing the internet, and usage of applications to set the benchmark of the normal behaviour of each employee.
-
Anomaly Detection: Through the analysis of the patterns and the deviations, Time Champ can help to detect suspicious activities which may include unauthorized access, leakage of data, or any other security threats.
-
Real-time Alerts: These notify the administrators or security teams when they identify any suspicious activities for possible threats to be dealt with.
Conclusion
Therefore, it is crucial to recognize and address the signs of employees’ suspicious activity in the workplace to prevent security threats and ensure the organization’s efficiency. Through training, policy development, and behaviours supervision organizations can reduce risks and protect their business. This implies that companies should prioritize detecting and preventing suspicious activities to minimize the occurrence of dangerous events that could harm the business and its employees.
Detect suspicious activities in your workplace with Time Champ!
Get a Demo Today and Ensure a Secure Work Environment Like Before!
SignUp for FreeBook DemoFrequently Asked Questionss
Through effective security measures, training on identifying suspicious activities, supervising employees, and encouraging them to report suspicious activities.
Businesses can avoid the occurrence of suspicious activity by making sure that employees report any suspicious activity, having clear policies and consequences for such actions, and emphasizing ethical behavior.
Signs of employees’ suspicious activity in the workplace include changes in behavior, unexplained absence, unusual computer usage, access to restricted information, and financial irregularities.
If one has a
feeling that an employee
is involved in a certain
malpractice, then they
should report the matter
to the relevant
authorities in the
organization, collect
any proof secretly, not
confront the suspected
employee, and maintain
secrecy during the
investigation.