What if a tiny gap in your network could cause massive data losses, leaving your business exposed to fines and a damaged reputation? That’s the reality without strong protections in place. Network data loss prevention (DLP) is the safeguard your business needs. In this article, we’ll dive into how DLP can shield your data and keep your company secure.
What is Network Data Loss Prevention?
Network DLP is the most important technology developed to secure sensitive information across an organization’s network. This technology monitors, controls, and secures data in motion, including email communications, web applications, and file transfers. Network DLP solutions prevent organizations from accessing and leaking information through various channels.
Why is Network DLP Important for Businesses?
Network Data Loss Prevention (Network DLP) is vital. It will keep secret info safe from unauthorized access within an organization. It will also ensure compliance with regulations. As more companies rely on digital communication, the risk of data breaches and unauthorized access is rising. Network DLP prevents these risks. It tracks data in motion and stops leaks of sensitive info through emails and file transfers.
The first reason for adopting Network DLP is that most data security laws are strict. They include GDPR, HIPAA, and PCI DSS. These laws insist that personal data and sensitive information must be protected suitably. If a business doesn’t follow the law, it will have to face significant fines and damage its reputation. Network DLP solutions prove an organization’s commitment to data security and compliance. They can monitor and automate generated reports.
Network DLP gives better insight into user behavior and data access in an organization. It boosts awareness of insider threats and protects against data leaks from human errors. Network DLP protects intellectual property by controlling sensitive information. It also raises security awareness as employees access or share that information.
How Network DLP Works
Network DLP is more than basic software. It is a smart, watchful system. It tracks and protects sensitive information in real-time. Let’s dive into how it all works to keep your data exactly where it should be.
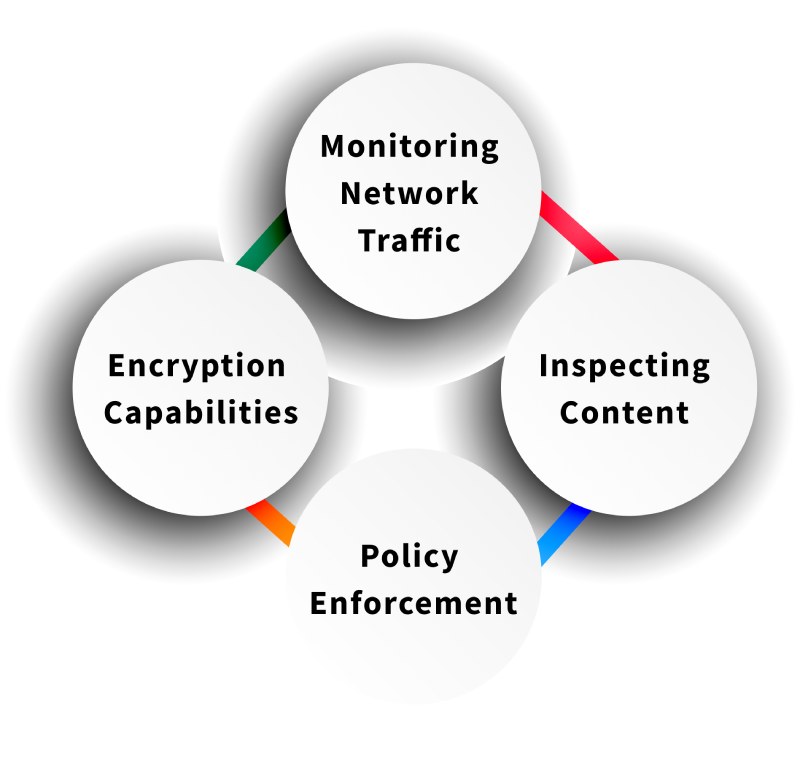
1. Monitoring Network Traffic
Network DLP scans the network in real time for any unauthorized data breach or data transfer and flags it appropriately. This involves analyzing data packets as they flow through the network. This includes emails, file transfers, and web app interactions. By actively tracking this traffic, network DLP solutions detect unusual activity or suspicious actions that allow organizations to prevent the leakage and misuse of sensitive information.
2. Inspecting Content
After monitoring network traffic, network DLP solutions inspect the content within the data packets. This inspection process scans for specific types of sensitive information, such as personal data (PII), financial records, or intellectual property. DLP tools use advanced techniques, like pattern recognition and machine learning. They accurately identify and classify sensitive data. This scan ensures that sensitive data follows the security policies.
3. Policy Enforcement
Once sensitive information is identified, the predefined company policies of network DLP implementations are enforced on that data as well. Policies determine what actions are taken if data is flagged as sensitive, whether it’s restricting access, blocking certain actions, or alerting security personnel. For example, once a user attempts to transfer sensitive data out of an organization, the DLP will either block the transmission or notify the security team. Network DLP cuts down the risk of both inadvertent and intentional data leakage by enforcing such policies.
4. Encryption Capabilities
To further protect sensitive information, most network DLP solutions include encryption features. Data loss prevention tools will automatically encrypt the content if it includes sensitive information transmitted over the network. The content becomes unreadable to the user who does not have access to read the same. Even if data was intercepted, access would not be possible to data as decryption keys are required. Combining encryption with network DLP adds security. It helps meet regulations and protect data privacy.
Benefits of Implementing Network DLP
Why consider network DLP? It’s not just about stopping data leaks. Network DLP protects sensitive information and builds client trust. It offers real, valuable benefits. Let’s explore why it’s worth it.
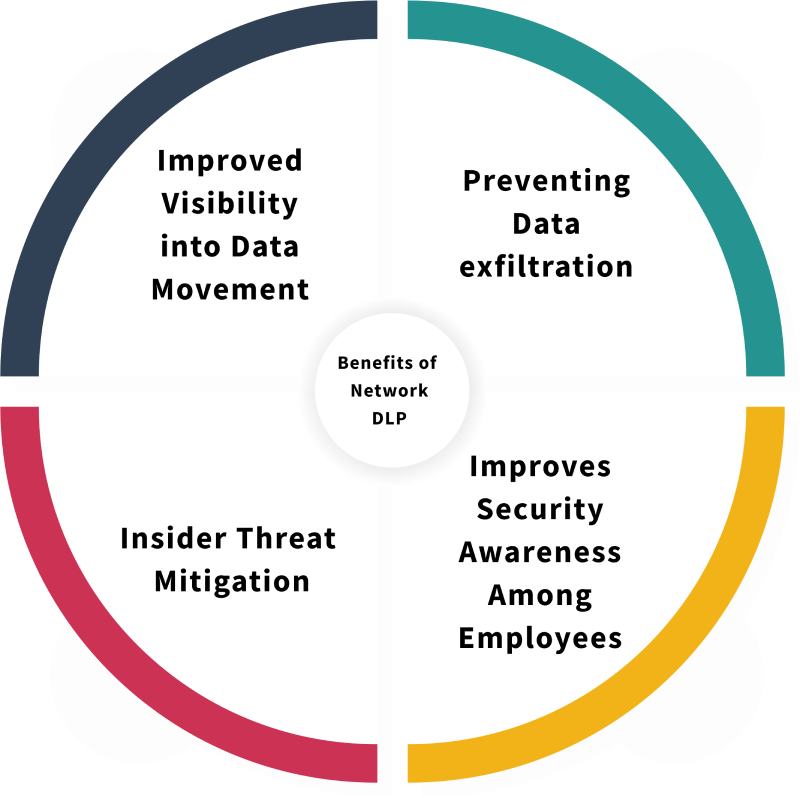
1. Preventing Data Exfiltration
The most important benefit of network DLP is its capability to prevent data exfiltration. DLP solutions can monitor network traffic. They can then block unauthorized attempts to send sensitive information outside the organization. This proactive approach protects critical data from external threats and leaks. It cuts the risk of data breaches that could cause financial loss and reputational damage.
2. Improves Security Awareness Among Employees
Network DLP promotes data security. It reinforces policies employees see daily. DLP restrictions remind staff of best practices for sensitive data. This helps build responsible data habits. This awareness, over time, cuts data leaks and boosts security. Employees gain a clear understanding of the importance of protecting information.
3. Insider Threat Mitigation
The other important advantage of network DLP is its strength in countering insider threats. Employees generally have access to sensitive data. Therefore, an organization can identify suspicious activity and take the needed actions. It guards IP while also creating a culture of accountability and security among employees.
4. Improved Visibility into Data Movement
The network DLP improves visibility in the movement of data within the organization. The DLP solutions notify the security teams about which sensitive information is accessed, shared, and transferred. From this point, they know the potential vulnerabilities that have to be addressed. With increased visibility organizations can fine-tune their data protection strategies so that sensitive information is never compromised while still operating efficiently. Overall, this comprehensive oversight is crucial for strengthening an organization’s cybersecurity framework.
Common Use Cases for Network DLP
By 2025, cybercrime is projected to reach a staggering $10.5 trillion in global costs. With such serious risks ahead, businesses must understand how network data loss prevention can help. DLP is essential for protecting sensitive information and avoiding data breaches. Let’s explore some common use cases where network DLP can make a real difference.
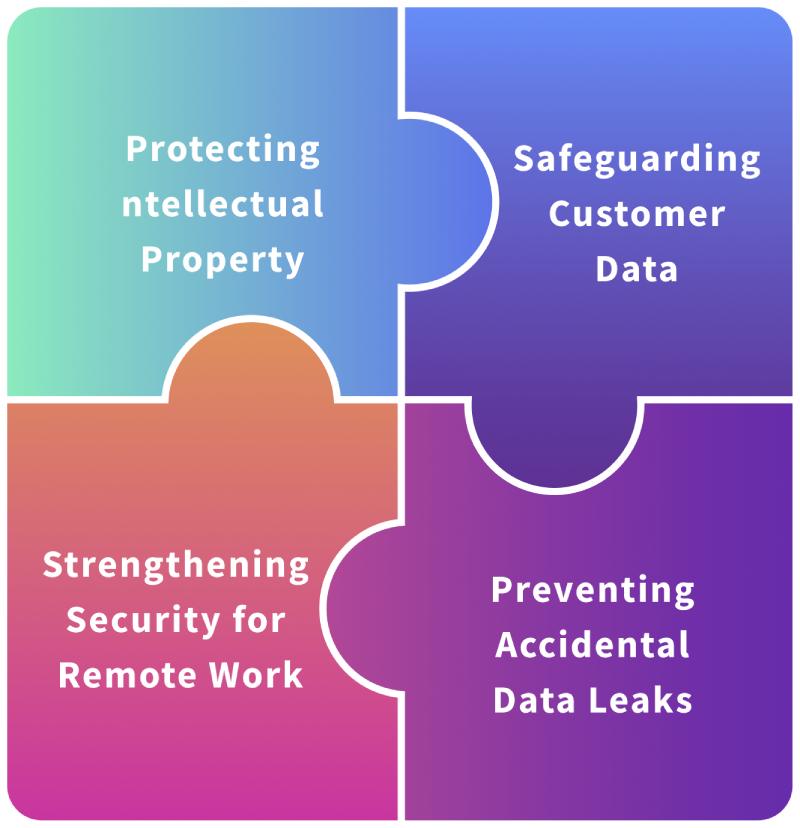
1. Protecting Intellectual Property
One of the precious assets of any organization is its intellectual property, things such as product designs, innovative ideas, and research. Network DLP protects this treasure. It monitors data flow and blocks any unauthorized sharing. This safeguards that your unique ideas and your competitive advantage remain exclusively yours.
2. Safeguarding Customer Data
Customers trust you with their sensitive information and network DLP helps you keep that trust intact. By closely monitoring how data moves, it catches any attempts to transfer customer data without permission. That protection is vital. It prevents breaches and builds trust with clients who rely on you to keep their information safe.
3. Preventing Accidental Data Leaks
This can happen to anyone sometimes with just a wrong email address or an incorrect upload. The network DLP minimizes the risk by flagging sensitive data before it leaves the network. That is having a safety net, allowing employees to go about their work confidently but minimizing the chances of an unintentional error.
4. Strengthening Security for Remote Work
As more people get accustomed to working from home, securing data in various locations is necessary. Network DLP supports remote work by monitoring the movement of data on all devices and ensuring that every location provides your team with an equal level of protection. This means that a remote team can be well-connected and productive without jeopardizing the security of the data.
Challenges in Network DLP Implementation
Putting network data loss prevention (DLP) in place can strengthen your data security, but it comes with its own set of challenges. Organizations often deal with tricky compliance regulations and pushback from users. Let’s dive into these common hurdles that teams face.
1. Complexity of Integration
A major issue with implementing network DLP is the integration into the current systems and workflows. Most organizations have multiple tools and technologies. The DLP solution has to work well with these tools, which is not an easy task. Integration might demand extended setup and customization, which consumes a lot of time and resources.
2. User Resistance and Adoption
Employees may not want to adopt network DLP since they believe it increases the monitoring and constrains their work. Such reluctance will negatively affect the successful implementation and effectiveness of this technology. Organizations must present the advantages of DLP, emphasizing how it protects both the company and its employees’ data.
3. High Volume of False Positives
Network DLP solutions are bound to raise several false positives, making harmless actions flagged as malicious. This just results in alert fatigue and pulls the focus off critical risks for the parts of security teams. Organizations should improve their DLP settings. They should use machine learning to reduce false positives to an acceptable level. This will cut inaccuracies.
4. Evolving Threat Landscape
Cyber security threats are constantly changing patterns due to new vulnerabilities or new methods of attack. Keeping DLP solutions updated and effective against these evolving threats can be a significant challenge. This is a huge task for organizations. They must stay aware of new threats. So, they must constantly update their DLP to meet their needs.
Best Practices for Network DLP Deployment
“An ounce of prevention is worth a pound of cure.” — Benjamin Franklin. This quote comes quite in handy when talking about network DLP. With the continuously rising cyber threats, having best practices for DLP deployment is important. So, let’s look into the best strategies to safeguard your sensitive data effectively.
1. Assess and Define Clear Data Protection Goals
Before implementing network DLP, first, define what you intend to protect and why. These include sensitive data types, for instance, customer information, IP, financial records, and so on. Defining these priorities will shape the DLP strategy with the needs of your organization and ensure that the proper data is protected.
2. Set Clear and Flexible Policies
Network DLP policies should be clear, targeted, and adaptable. Begin with those data types that are most sensitive and then modify them progressively. Flexible policies ensure there is no unnecessary restriction from the DLP system such that employees remain productive, hence the DLP system accommodates the evolving security demands.
3. Provide Employee Training and Awareness
Network DLP works best when employees understand its purpose. Regular training sessions on data protection, DLP policies, and safe data-sharing practices help build this understanding. Once awareness is created, organizations reduce data leaks. They evolve a security culture, which drives DLP closer to daily operations.
4. Conduct Regular Audits and Assessments
Regular audits will help to examine the effectiveness of your DLP policies and systems. Based on logs that are reviewed and incidents, organizations will know the exact areas of improvement, determine compliance, and even fine-tune their data protection strategies. Audits provide an indication of the performance of your DLP system and the spots where adjustment is needed.
Get Started with Time Champ’s DLP
Time Champ is a powerful solution for organizations looking to enhance their network data loss prevention efforts. With its advanced features, Time Champ helps protect sensitive information from unauthorized access and potential leaks, ensuring your data remains secure.
-
Limiting access to critical data online helps reduce the risk of unauthorized exposure, allowing only authorized personnel to access sensitive information.
-
The USB access control feature restricts connections to approved devices, preventing data leaks from untrusted external sources and boosting overall security.
-
Real-time file monitoring tracks data movements across the network, enabling quick responses to any suspicious activity and effectively mitigating potential threats.
-
Regulating file transfers ensures that only authorized actions occur on the network, safeguarding sensitive data during transmission.
Time Champ safeguards sensitive data and empowers organizations to streamline compliance efforts and maintain regulatory standards. Integrating robust security features fosters a culture of data protection, enabling teams to focus on productivity while ensuring data integrity.
Conclusion
In short, network DLP protects
sensitive data. It helps your
organization meet industry
standards. A proper DLP strategy
protects you from data leaks. It
also guards against malicious
threats. It does this by monitoring,
detecting, and managing data flow in
and out of your network.
As
cyber threats continue to grow,
using a robust DLP solution is the
most proactive step you can take to
protect your organization’s
assets and create a secure digital
environment. Building this robust
defense protects your data and helps
to maintain confidence in the minds
of clients.
Ready to enhance your data security?
Discover how Time Champ's comprehensive DLP solution can shield your business from costly data breaches.
Signup for FreeBook DemoFrequently Asked Questions
Policies relating to Network DLP need to be reviewed and revised every six months or even immediately if significant changes have taken place in your organization or the regulatory environment. In this way, the policies remain effective against continually changing threats and can evolve as your business practices change or new types of sensitive information emerge.
In regard to network DLPs, several classifications include content-based DLP, focusing on sensitive information within data transfers; network-based DLP observes data in motion across a network; and endpoint-based DLP guards sensitive information on individual devices. Thus, each is important and integral to securing your business’s information.
The network DLP protects information during its transfer across a network in an effort not to leak data without consent, whereas the endpoint DLP protects information stored within individual devices that may not need to be accessible to particular people. They both form a complete and comprehensive means of securing your organization’s sensitive data.
Network DLP solutions help various types of industries, for example: finance, health care, retail, education, and technologies. All those sectors process sensitive information regarding financial accounts, patient care, client payment details, and intellectual property. Deployment of the network DLP prevents any data breach along with helping in maintaining regulations of every industry.