Every Keystroke Matters: Keylogger Software for Precise Employee Monitoring
Detect malicious activity and optimize productivity through keystroke logging, streamlining employee monitoring and enhancing workplace security.

Detect malicious activity and optimize productivity through keystroke logging, streamlining employee monitoring and enhancing workplace security.
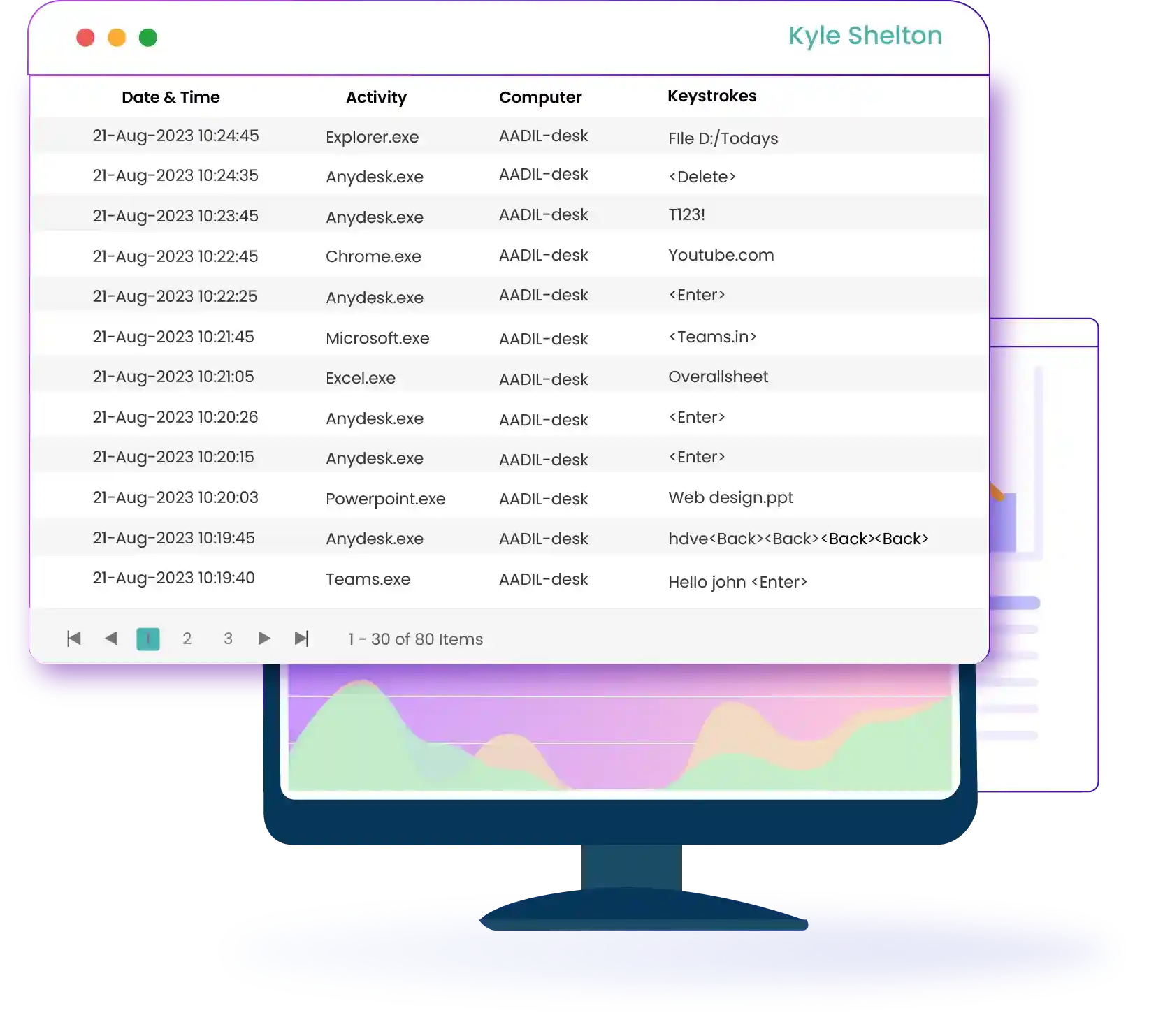
Time Champ, bundled with Keystroke Logger Software, provides a clear picture of employee work habits as it records each and every keystroke made. The applications of its use are immense, ranging from improving performance analysis to strengthening protection from internal threats. This is a crucial attribute that will facilitate the monitoring of remote and on-site workers for a complete trail of their keyboard movements, like inputting texts or copying and pasting some content.
The benefits? Enhanced productivity, increased security, and actionable data for improving management decisions. Time Champ’s keystroke logger offers a vital companion in today’s world, be it for performance optimisation, security, or data protection purposes. It helps simplify complex tasks while still respecting individual's privacy, maintaining a transparent and efficient corporate culture.
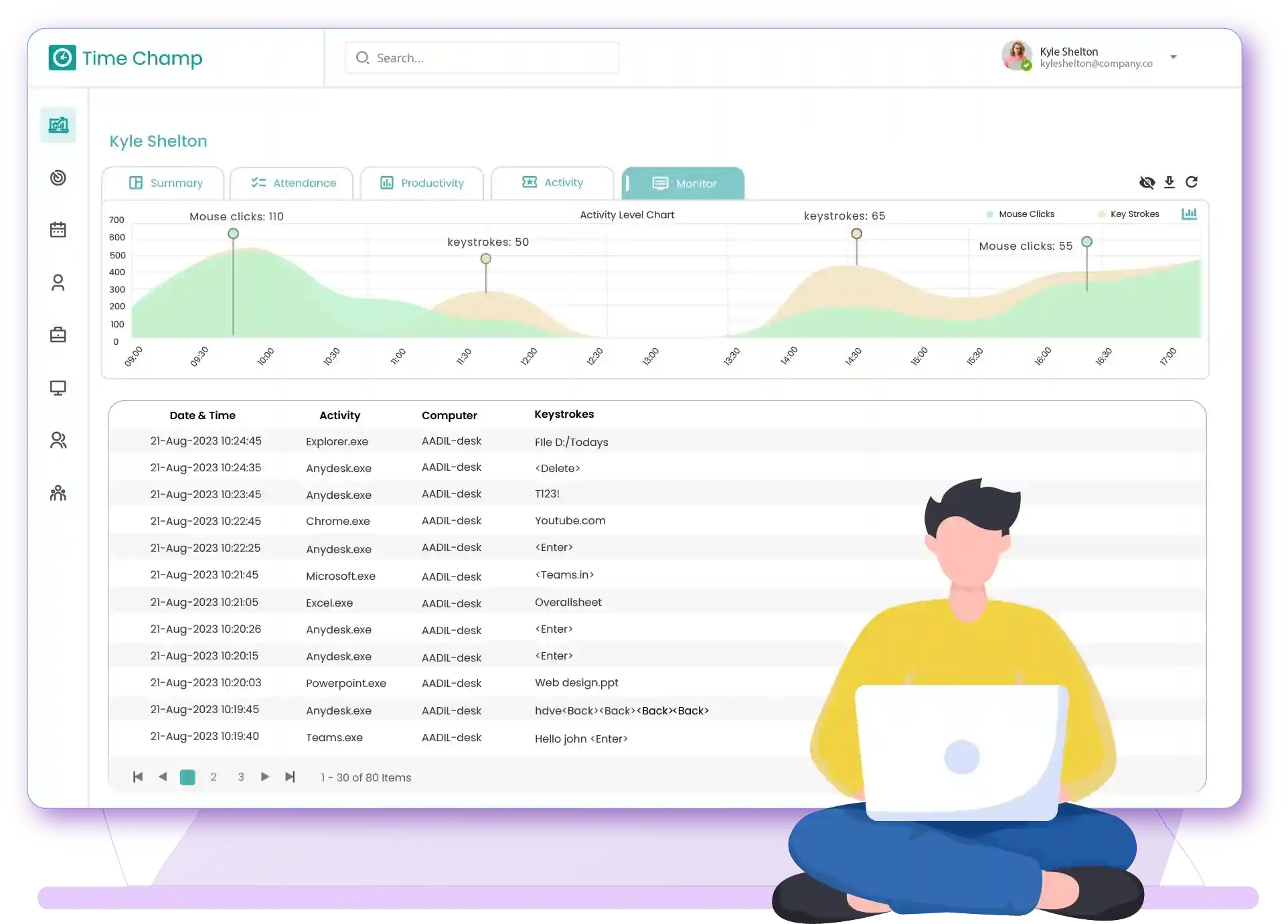
Keystroke monitoring, also known as keylogging, is the process of recording the keys struck on a keyboard. In the context of work environment, it refers to monitoring of every single word and command input by any employee in any platform; browsers, e-mails, office applications, or programs. This is more than just about surveillance, this is about understanding and improving workflow efficiency. Using this key logger software responsibly could be a good tool for business, helping monitor employees' activities, ensure accurate data, and protect from possible security threats.
The Keystroke logging feature of Time Champ easily integrates with other features such as activity monitoring, time-tracking, productivity tracking and project management to provide a precise understanding of keyboard usage, and productivity insights and makes it an essential asset in modern workplaces.
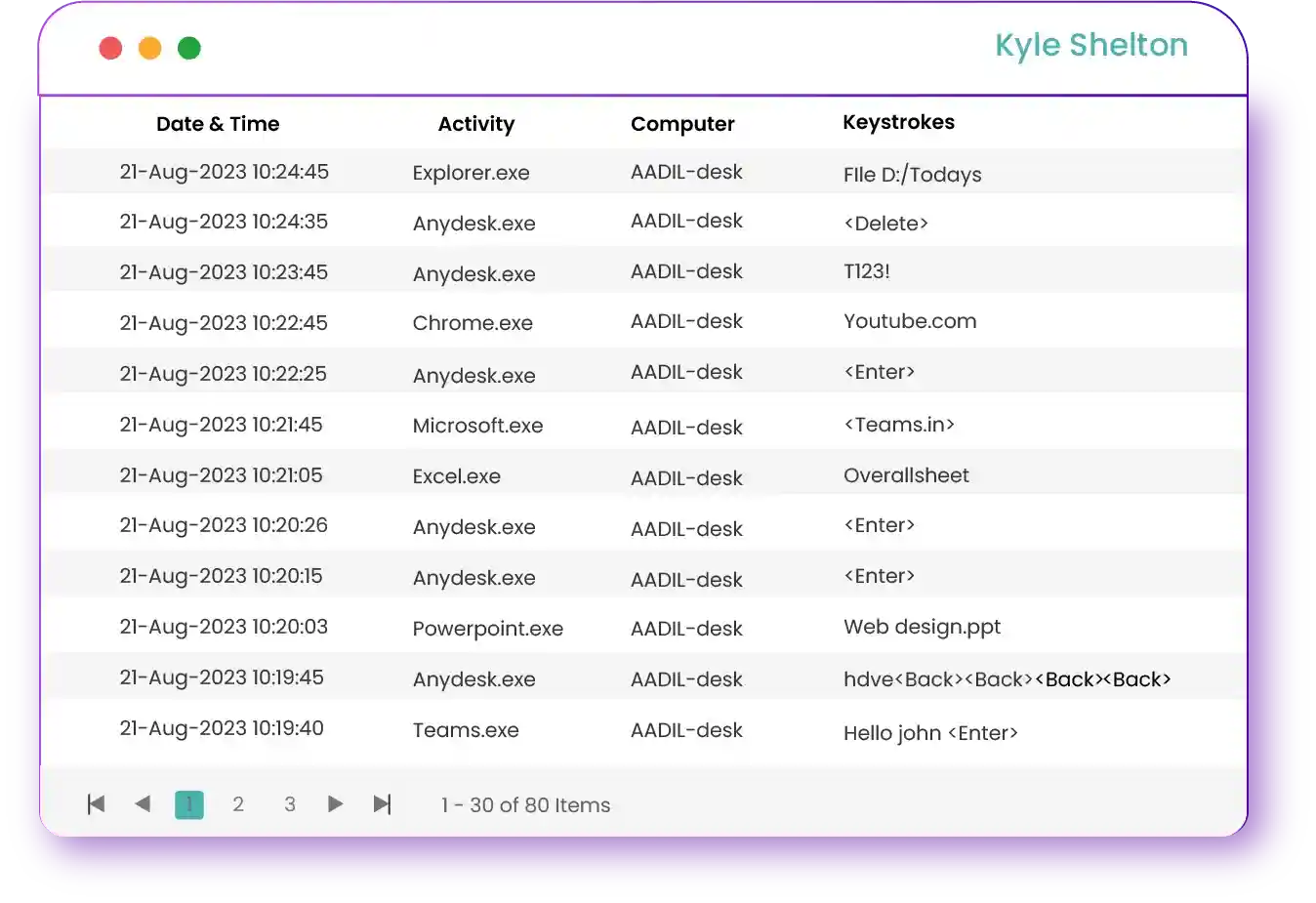
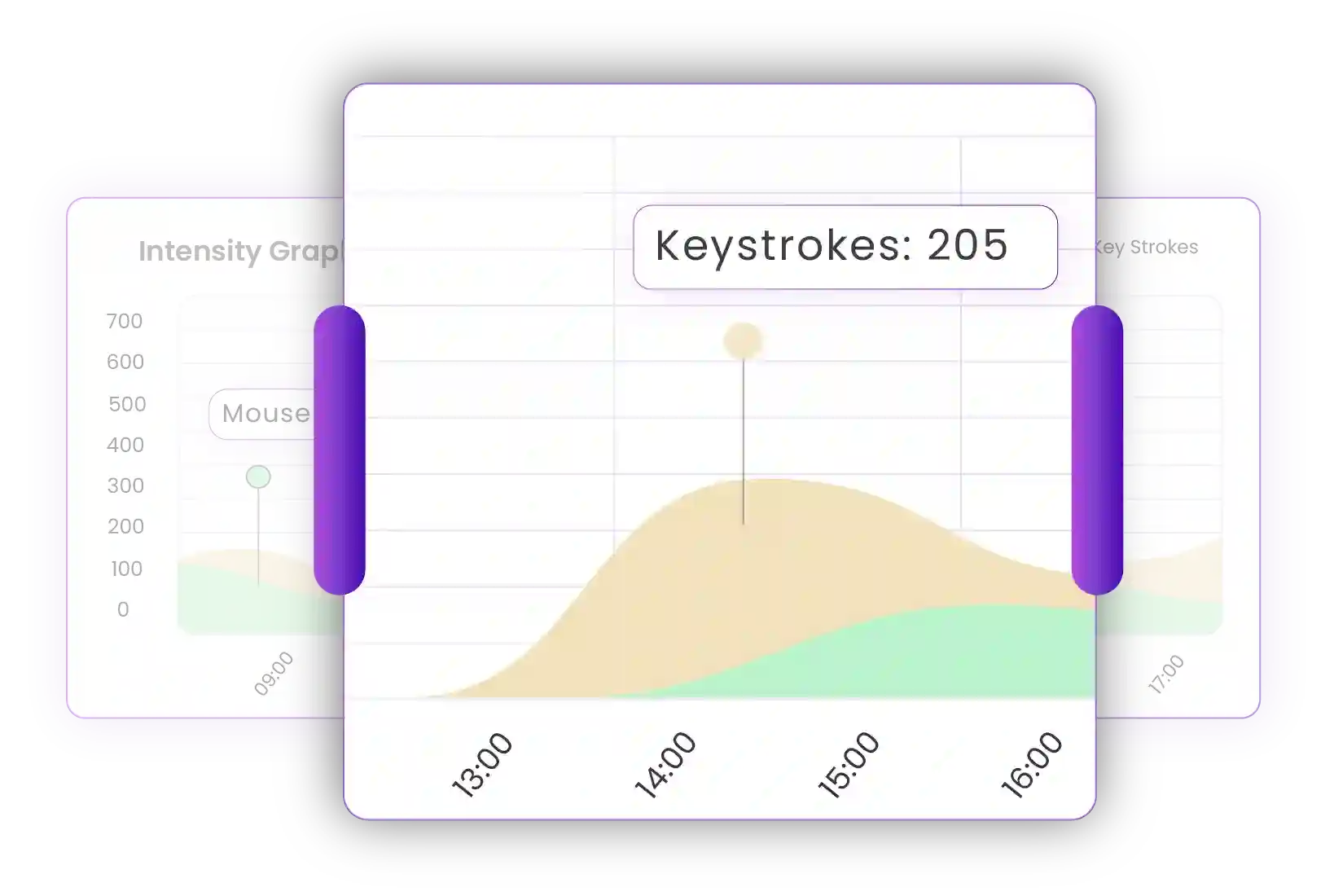
Time Champ's keystroke logger delves deep into every tap and press, capturing every single keystroke with the outmost accuracy Such detailed recording allows for an in-depth analysis of employee work patterns, offering a granular view of daily activities.
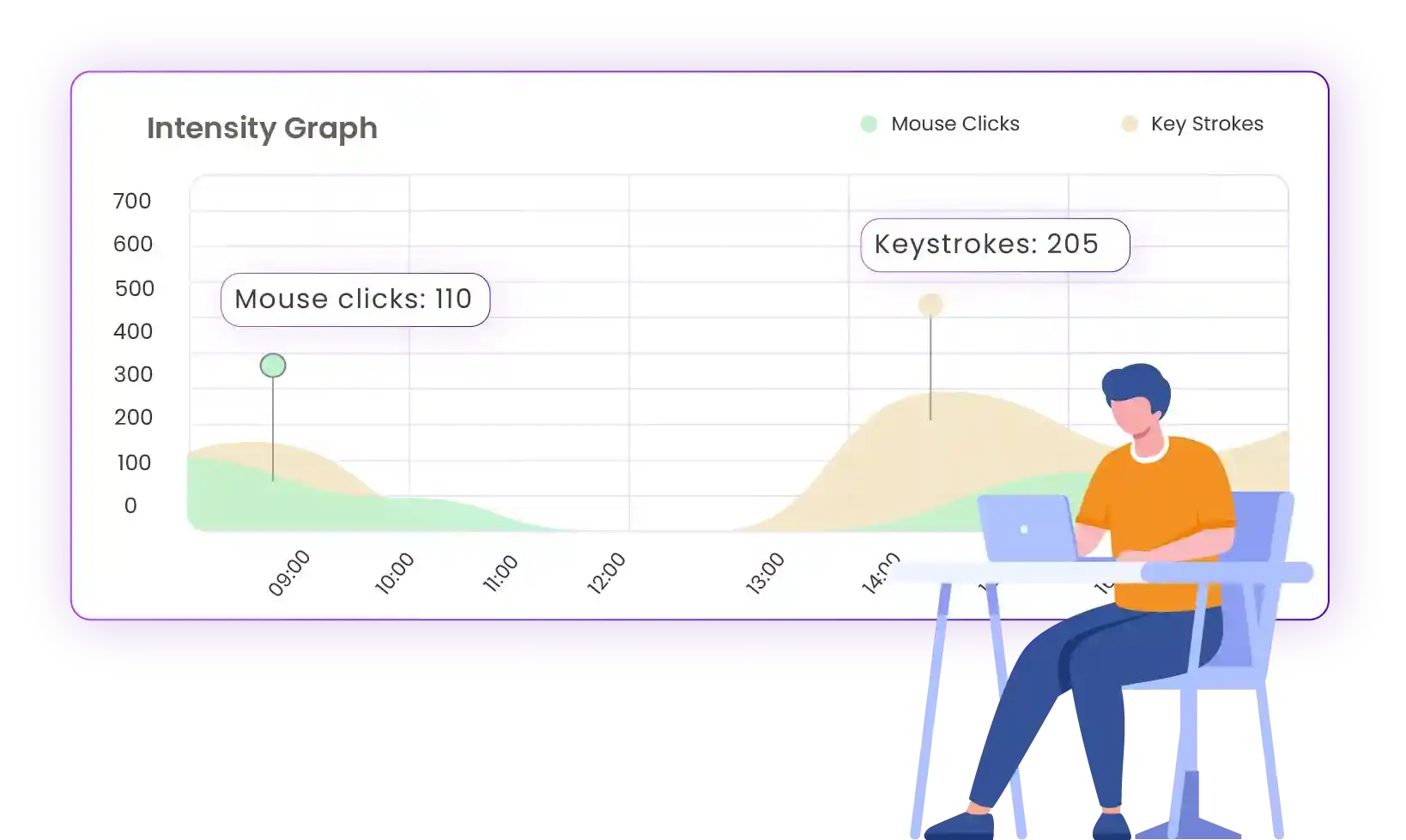
With the innovative graphs introduced by Time Champ, visualizing work intensity becomes effortless. These visualizations display the intensity and frequency of keystrokes during specific times giving a clear picture of employee engagement and workload distribution.

Vigilance is most important in maintaining workplace security. Our keystroke logger software can detect suspicious keystroke patterns and alert the supervisors immediately with the custom suspicious alerts; hence, enabling immediate action that protects against potential threats.
Time Champ makes it easy to go back to historical data. These records of keystrokes at specific times are invaluable for managers at times of performance reviews, compliance checks and more
Enhanced Productivity: Keystroke logging provides insights into the work patterns of employees which helps in identifying areas for productivity improvement.
Enhanced Security: Keylogging acts as a frontline defence against security breaches, offering real-time alerts on suspicious activities.
Employee Monitoring: It offers a transparent mechanism for monitoring employee activities, making sure that work time is well utilized.
Compliance and Auditing: The keystroke recorder software helps to stay compliant with regulations and simplifies the auditing process.
Training and Support: Insights from keystroke logging can be very useful in employee training and support programs.
Reduction of Malicious Insider Threats : The software helps in early detection of insider threats by monitoring keystroke patterns.

Keystroke data provides a quantifiable measure of employee performance which can help managers in making informed decisions.
Keystrokes monitoring helps ensure the accuracy of data entry tasks; it reduces errors and enhances data integrity.
Through keystroke pattern analysis the potential insider security threats can be detected early.
Insights into keystroke patterns helps in optimizing time management strategies within the team.

Keylogging is particularly important in tracking the performance of remote employees to make sure that their productivity remains consistent.
The IT team can use keystroke logs to diagnose issues and deal with them promptly.
Keyboard logger programs can catalogue the creative and developmental processes of employees, thus recording the evolution of innovative projects.
In the instances of suspected data breaches or regular audits, the data from Keyloggers serve as vital tools , providing indisputable evidence in investigations
Keylogging is legal in a business context when used ethically and with openness. Employers must make sure the monitoring complies with privacy regulations and notify staff members about it. Time Champ makes sure that all keylogging operations are carried out morally and strictly in accordance with the law. Our approach to implementing keylogging tools is centred on transparency and compliance with privacy legislation.
Only authorised personnel within the company, like managers or IT security teams, have access to recorded keystroke data. By ensuring that sensitive information is handled responsibly and in accordance with compliance rules, this precaution is essential for preserving data privacy and security.
With its strong security features, Time Champ's keylogger software greatly lowers the possibility of tampering or degradation. These measures are designed to uphold the integrity and functionality of the keylogging software, maintaining reliable and uninterrupted monitoring.
The Time Champ keylogger is designed with discretion and efficiency in mind. It discretely runs in the background, capturing keystrokes without interfering with regular company processes or taking up large amounts of time. This guarantees a smooth integration.
Keystroke logging along with detailed analysis of work patterns, helps in identifying areas where productivity can be improved. Managers can enhance employee performance and productivity by optimising task allocation and streamlining workflows with this data-driven strategy.
Keystroke records are very useful for auditing and compliance. They ensure that all actions are traceable and comply with regulatory standards by offering an accountable and comprehensive record of employees' activity. This aspect of keylogging can be essential for maintaining transparency and upholding industry standards.
Yes, Keystroke tracking provides valuable insights that are useful in determining areas of skill gaps and training needs to improve employee skills and increase overall workplace competency.
Keylogging provides a clear and efficient way to keep an eye on employees' activity when they work remotely. It helps to maintain consistent employee engagement and productivity, irrespective of the worker's location, promoting a reliable and effective remote work environment.
Time Champ's keystroke recorder is adept at detecting potential insider threats by monitoring for unusual keystroke patterns or specific keyword usage. It sends specious alerts when unusual or suspicious key patterns are detected. This proactive approach enables early identification and prevention of risks, improving organizational security.
Time Champ places a high priority on data security by using stringent access control procedures and cutting-edge encryption. These protocols ensure that all keystroke data remains secure, confidential, and protected against unauthorized access, aligning with the highest standards of data protection.
The majority of modern keylogging software is made to be discreet, light-weight, and have little effect on system performance. However, the effect could change based on the complexity of the software and the specifications of the system.
Yes, advanced keylogging software provides a complete picture of user activities by recording clipboard data, tracking application usage, taking screenshots, and monitoring internet activity.